Business
DOJ charges 7 Chinese spies with targeting US political leaders, major businesses

From LifeSiteNews
By Matt Lamb
The hackers ‘spent approximately 14 years targeting U.S. and foreign critics, businesses, and political officials’ as part of a massive Chinese espionage operation, according to the DOJ.
Hackers targeted defense contractors, American political leaders, and U.S. companies with malware as part of a surveillance operation for the Chinese Communist Party, the Department of Justice (DOJ) alleges.
The DOJ released details on the indictment of seven Chinese individuals who have been charged with “conspiracy to commit computer intrusions and conspiracy to commit wire fraud,” according to a Monday news release.
The individuals are part of a People’s Republic of China (PRC) group who “spent approximately 14 years targeting U.S. and foreign critics, businesses, and political officials in furtherance of the PRC’s economic espionage and foreign intelligence objectives,” according to the DOJ.
Officials unsealed the indictment on Monday, though charges were originally filed in January.
The indictment provides further insight into how the CCP targets American companies and political leaders for retribution and influence using computer viruses.
The CCP and its Ministry of State Security “sought to obtain information on political, economic and security policies that might affect the PRC, along with military, scientific and technical information of value to the PRC,” the indictment states. “Among other things, the MSS and its state security departments focused on surreptitiously identifying and influencing the foreign policy of other countries, including the United States.”
The hackers used a front company called Wuhan XRZ beginning in at least 2010. They would send fake emails to U.S. senators, business leaders, and information technology companies looking to gain access. They were successful in hacking defense contractors, information technology providers, and universities, among other victims.
The DOJ itself was targeted, along the Commerce Department, the Treasury Department, and the White House.
The Justice Department alleges:
These computer network intrusion activities resulted in the confirmed and potential compromise of work and personal email accounts, cloud storage accounts and telephone call records belonging to millions of Americans, including at least some information that could be released in support of malign influence targeting democratic processes and institutions, and economic plans, intellectual property, and trade secrets belonging to American businesses, and contributed to the estimated billions of dollars lost every year as a result of the PRC’s state-sponsored apparatus to transfer U.S. technology to the PRC.
The “Conspirators,” as they are called in the filing, began sending out phishing emails in at least 2015, according to the DOJ. The emails would look like they were from “prominent American journalists” with excerpts from news sites.
“If the recipient activated the tracking link by opening the email, information about the recipient, including the recipient’s location, IP addresses, network schematics and specific devices used to access the pertinent email accounts, was transmitted to a server controlled by the Conspirators,” the DOJ stated. “The Conspirators used this method to enable more direct and sophisticated targeting of recipients’ home routers and other electronic devices, including those of high ranking U.S. government officials and politicians and election campaign staff from both major U.S. political parties.”
In just a few months in 2018, the hackers “sent more than 10,000 malicious email messages” to “high-ranking U.S. government officials and their advisors, including officials involved in international policy and foreign trade issues.”
They also targeted campaign staff for “a presidential campaign” in 2020. The filing does not state which campaign.
European Union and United Kingdom leaders who were part of the anti-Communist Inter Parliamentary Alliance on China were also targeted.
Other victims included: “a nuclear power engineering company,” a defense contractor, an aerospace contractor, and “a leading American manufacturer of software and computer services based in California.”
Telecommunications companies, law firms, and steel companies were also targeted.
The CCP impersonated real steel companies in order to gain access to their emails during a battle over tariffs on China. After the Trump administration announced new steel tariffs in 2018, the hackers “registered a malicious domain impersonating the legitimate domain of one of the largest steel producers in the United States (the ‘American Steel Company’)” as well as the International Steel Trade Forum.
“These malicious domains allowed the Conspirators to communicate with malware they installed on the network of the American Steel Company to access and surveil the victim,” the DOJ stated.
They also targeted the Norwegian government in 2018 because it was considering awarding the Nobel Prize to Hong Kong democracy activists.
The PRC is a “malicious nation state,” a federal prosecutor stated in the DOJ news release.
“These allegations pull back the curtain on China’s vast illegal hacking operation that targeted sensitive data from U.S. elected and government officials, journalists, and academics; valuable information from American companies; and political dissidents in America and abroad. Their sinister scheme victimized thousands of people and entities across the world, and lasted for well over a decade,” U.S. Attorney Breon Peace for the Eastern District of New York stated in the news release.
“America’s sovereignty extends to its cyberspace. Today’s charges demonstrate my office’s commitment to upholding and protecting that jurisdiction, and to putting an end to malicious nation state cyber activity.”
Business
Chinese firm unveils palm-based biometric ID payments, sparking fresh privacy concerns

By Ken Macon
Alipay’s biometric PL1 scanner uses vein and palm-print data for processing payments, raising security concerns over the storage and use of permanent biometric data.
Alipay, the financial arm of Alibaba, has introduced a new palm-based biometric terminal, dubbed the PL1, which enables individuals to make purchases simply by presenting their hand – no phone, card, or PIN required. Positioned as a faster, touch-free alternative for payment, this system reflects a growing industry shift toward frictionless biometric transactions.
At the core of the PL1 is a dual-mode recognition system that combines surface palm print detection with internal vein mapping. This multi-layered authentication relies on deeply unique biological signatures that are significantly harder to replicate than more common methods like fingerprints or facial scans. Alipay reports that the device maintains a false acceptance rate of less than one in a million, suggesting a substantial improvement in resisting identity spoofing.
Enrollment is designed to be quick: users hover their palm over the sensor and link their account through a QR code. Once registered, purchases are completed in around two seconds without physical interaction. During early trials in Hangzhou, this system reportedly accelerated checkout lines and contributed to more hygienic point-of-sale environments.
The PL1 arrives at a time of rapid expansion in the biometric payments sector. Forecasts estimate that more than 3 billion people will use biometrics for transactions by 2026, with total payments surpassing $5 trillion. Major players are already onboard: Amazon has integrated palm authentication across U.S. retail and healthcare facilities, while JP Morgan is gearing up for a national deployment in the same year.

Alipay envisions the PL1’s use extending well beyond checkout counters. It is exploring applications in public transit, controlled access facilities, and healthcare check-ins, reflecting a broader trend toward embedding biometric systems in daily infrastructure. However, while domestic deployment benefits from favorable policy conditions, international expansion may be constrained by differing legal standards, particularly in jurisdictions that enforce stringent rules on biometric data usage and consent.
Despite the technological advancements and convenience the PL1 offers, privacy remains a major point of contention. Unlike passwords or cards that can be reset or replaced, biometric data is immutable. If compromised, individuals cannot simply “change” their palm patterns or vein structures. This permanence heightens the stakes of any potential data breach and raises long-term concerns about identity theft and surveillance.
Alipay’s approach, storing encrypted biometric templates locally on devices and restricting data flow within national border, does address certain regulatory demands, especially within China, but the broader implications of biometrics are likely to be a growing privacy and surveillance concern in the coming years.
Business
Trump considers $5K bonus for moms to increase birthrate

 MxM News
MxM News
Quick Hit:
President Trump voiced support Tuesday for a $5,000 cash bonus for new mothers, as his administration weighs policies to counter the country’s declining birthrate. The idea is part of a broader push to promote family growth and revive the American family structure.
Key Details:
- Trump said a reported “baby bonus” plan “sounds like a good idea to me” during an Oval Office interview.
- Proposals under consideration include a $5,000 birth bonus, prioritizing Fulbright scholarships for parents, and fertility education programs.
- U.S. birthrates hit a 44-year low in 2023, with fewer than 3.6 million babies born.
Diving Deeper:
President Donald Trump signaled his support Tuesday for offering financial incentives to new mothers, including a potential $5,000 cash bonus for each child born, as part of an effort to reverse America’s falling birthrate. “Sounds like a good idea to me,” Trump told The New York Post in response to reports his administration is exploring such measures.
The discussions highlight growing concern among Trump administration officials and allies about the long-term implications of declining fertility and family formation in the United States. According to the report, administration aides have been consulting with pro-family advocates and policy experts to brainstorm solutions aimed at encouraging larger families.
Among the proposals: a $5,000 direct payment to new mothers, allocating 30% of all Fulbright scholarships to married applicants or those with children, and launching federally supported fertility education programs for women. One such program would educate women on their ovulation cycles to help them better understand their reproductive health and increase their chances of conceiving.
The concern stems from sharp demographic shifts. The number of babies born in the U.S. fell to just under 3.6 million in 2023—down 76,000 from 2022 and the lowest figure since 1979. The average American family now has fewer than two children, a dramatic drop from the once-common “2.5 children” norm.
Though the birthrate briefly rose from 2021 to 2022, that bump appears to have been temporary. Additionally, the age of motherhood is trending older, with fewer teens and young women having children, while more women in their 30s and 40s are giving birth.
White House Press Secretary Karoline Leavitt underscored the administration’s commitment to families, saying, “The President wants America to be a country where all children can safely grow up and achieve the American dream.” Leavitt, herself a mother, added, “I am proud to work for a president who is taking significant action to leave a better country for the next generation.”
-
 2025 Federal Election2 days ago
2025 Federal Election2 days agoOttawa Confirms China interfering with 2025 federal election: Beijing Seeks to Block Joe Tay’s Election
-

 2025 Federal Election1 day ago
2025 Federal Election1 day agoBREAKING: THE FEDERAL BRIEF THAT SHOULD SINK CARNEY
-

 2025 Federal Election2 days ago
2025 Federal Election2 days agoHow Canada’s Mainstream Media Lost the Public Trust
-

 2025 Federal Election2 days ago
2025 Federal Election2 days agoReal Homes vs. Modular Shoeboxes: The Housing Battle Between Poilievre and Carney
-

 2025 Federal Election1 day ago
2025 Federal Election1 day agoCHINESE ELECTION THREAT WARNING: Conservative Candidate Joe Tay Paused Public Campaign
-

 Media1 day ago
Media1 day agoCBC retracts false claims about residential schools after accusing Rebel News of ‘misinformation’
-
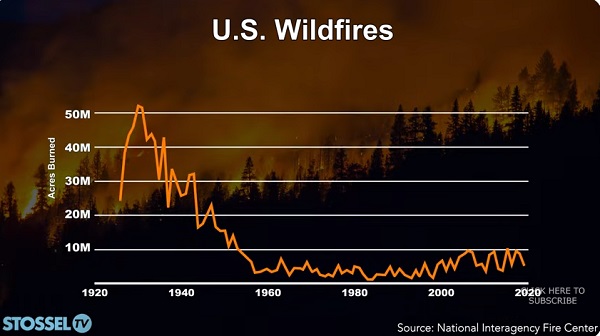
 John Stossel1 day ago
John Stossel1 day agoClimate Change Myths Part 2: Wildfires, Drought, Rising Sea Level, and Coral Reefs
-

 COVID-192 days ago
COVID-192 days agoNearly Half of “COVID-19 Deaths” Were Not Due to COVID-19 – Scientific Reports Journal






